WordPress malware: Don't let too-good-to-be-true deals infest your site
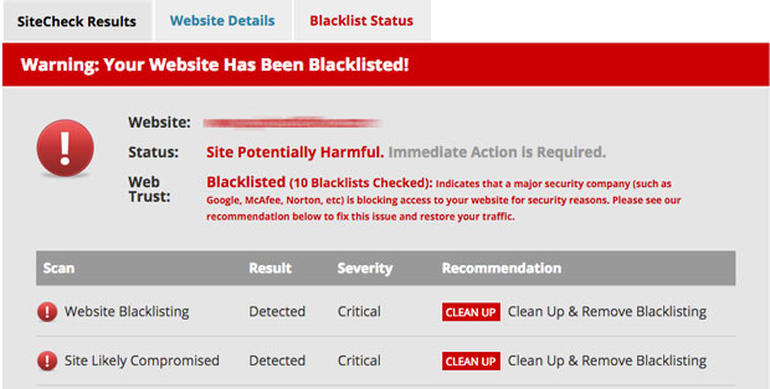
Sometimes you can smell when it's not going to end well. It's almost like there's a taste in the air. It started with a routine email message in my inbox. But after reading the first few words, I knew this was going to be one of those.
Here's how it started: “We bought the seamless donation plugin for our website…”
Naive bargain-hunters fall for this all the time. So now they've not only bought a theme with a malware payload, they've given their credit card information to the bastards at the same time. And then, when they use that theme or plugin, they're infecting all their visitors. Special.
The other variant, the one my user seems to have fallen for, is the one where popular free plugins (like the one I support) are downloaded by these same malicious merchants of maleficent malware and then posted on their stores and then sold.
In this case, naive site operators (who may not know to go to the WordPress.org plugin repository, but are just Googling their way to their doom) are giving money (and, again, their credit card and identity information) to the bad guys when they could have actually gotten it for free. Read the Rest of the Article Here….